Disruption of Lumma Stealer Infrastructure

Microsoft's Digital Crimes Unit (DCU) and international partners have successfully disrupted the Lumma Stealer, a prominent malware used to steal sensitive information and facilitate cybercrime. Legal actions were initiated on May 13, with the seizure of approximately 2,300 malicious domains that supported Lumma's operations. The Department of Justice (DOJ) also played a critical role in seizing Lumma's central command structure and disrupting online marketplaces selling this malware.

Image courtesy of Microsoft
Between March 16 and May 16, 2025, Microsoft identified over 394,000 Windows computers globally infected by Lumma. The takedown of these domains, many of which acted as user panels for Lumma operators, will effectively prevent criminals from accessing this malware to steal additional information. Redirecting seized domains to Microsoft sinkholes enables ongoing monitoring and intelligence gathering to bolster defenses against similar threats.
How Lumma Functions
Lumma operates as a Malware-as-a-Service (MaaS), allowing cybercriminals worldwide to deploy its capabilities for malicious campaigns. It has demonstrated a wide range of targets, being able to extract not only browser-stored passwords but also autofill data, email credentials, FTP client details, and two-factor authentication tokens.
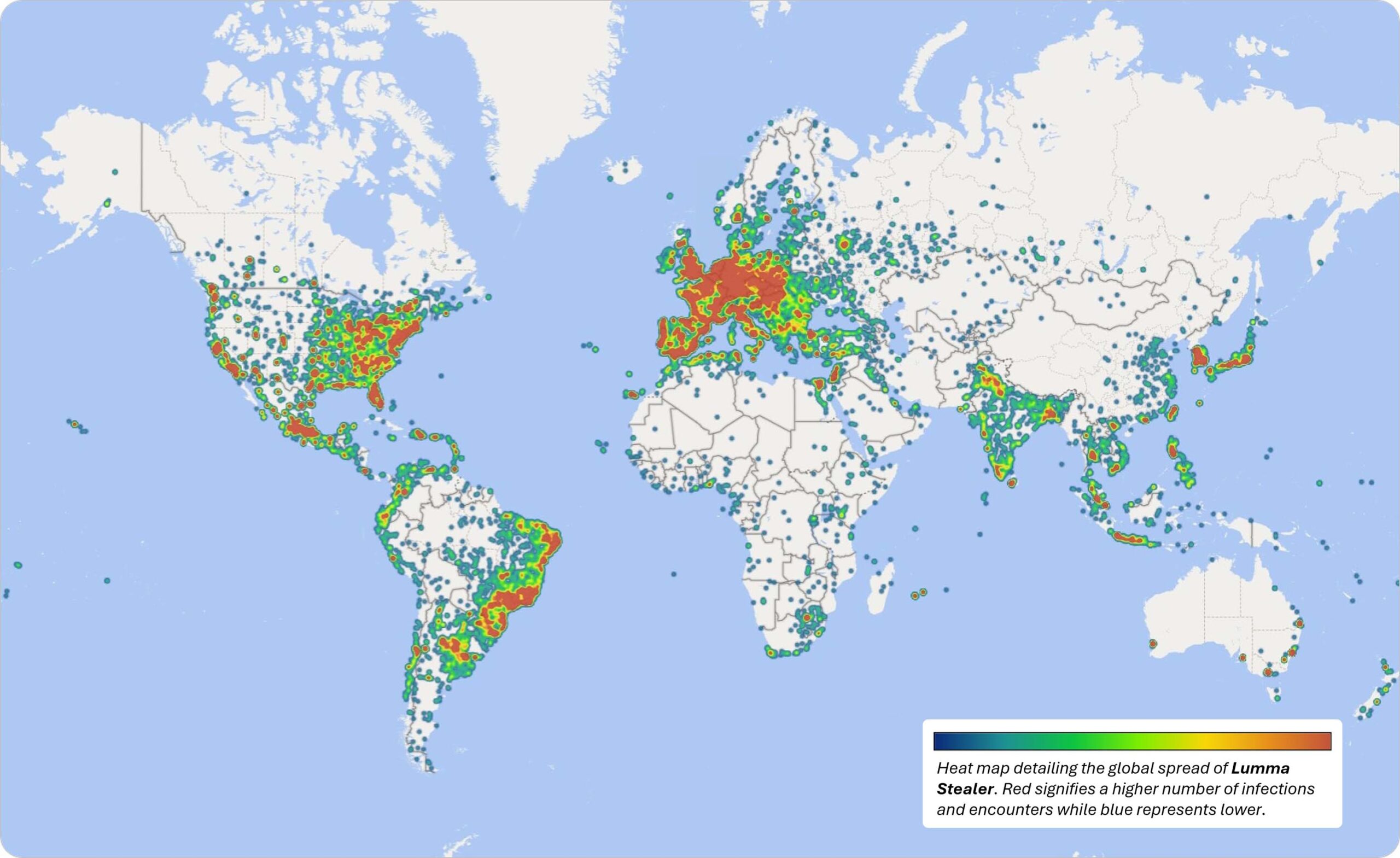
Image courtesy of Microsoft
According to Matthew R. Galeotti, head of the Justice Department’s Criminal Division, “Malware like LummaC2 is deployed to steal sensitive information such as user login credentials from millions of victims to facilitate a host of crimes, including fraudulent bank transfers and cryptocurrency theft.”
The Developer Behind Lumma
The primary developer of Lumma, operating under the alias "Shamel," is based in Russia and has been linked to the marketing of different tiers of Lumma services in underground forums. Due to its ease of distribution and ability to bypass security defenses, Lumma has been favored among cybercriminals. Shamel claimed to have “about 400 active clients” in an interview, highlighting the organized nature of this cybercrime operation.
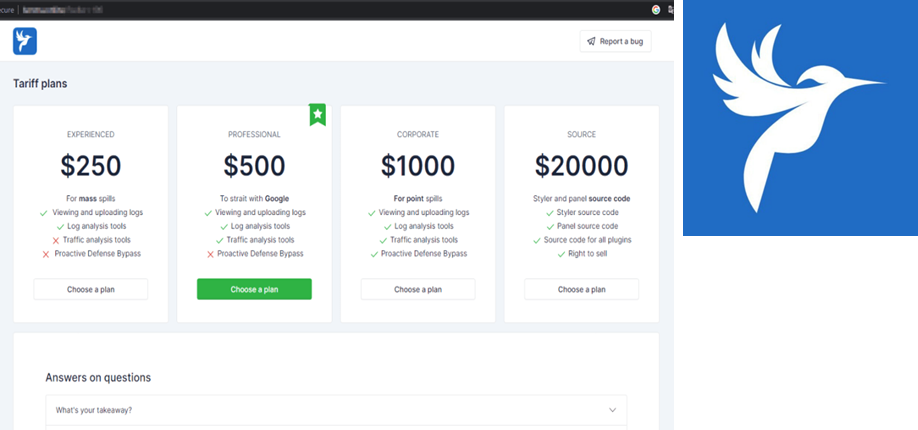
Image courtesy of Microsoft
Collaboration and Future Disruptions
Collaborative efforts between Microsoft, the DOJ, Europol, and Japan's Cybercrime Control Center have been essential in disrupting Lumma's infrastructure. By targeting such malware, authorities aim to create significant and lasting impacts on cybercrime operations. As Microsoft states, “Disrupting the tools cybercriminals frequently use can create a significant and lasting impact on cybercrime, as rebuilding malicious infrastructure and sourcing new exploit tools takes time and costs money.”
Protecting Against Information Stealers
Even with the Lumma infrastructure disrupted, the threat of information stealers remains real. Here are essential steps to reduce risk:
- Use strong, unique passwords for every account and consider a reputable password manager.
- Enable multi-factor authentication (MFA) whenever possible.
- Be cautious with emails and downloads, particularly those that appear as legitimate CAPTCHAs.
- Keep software and operating systems updated to patch vulnerabilities.
- Regularly monitor financial and online accounts for suspicious activity.
- Educate yourself about phishing and social engineering tactics.
For cybersecurity professionals, using advanced tools such as GrackerAI can enhance monitoring and response capabilities. GrackerAI is an AI-powered cybersecurity marketing platform designed to help organizations transform security news into strategic content opportunities. Explore how GrackerAI can assist your marketing team in identifying emerging trends and producing timely, relevant content that resonates with cybersecurity decision-makers.
Visit GrackerAI at https://gracker.ai to learn more about our services and how we can support your cybersecurity marketing efforts.




