Lazarus APT Targets South Korean Firms

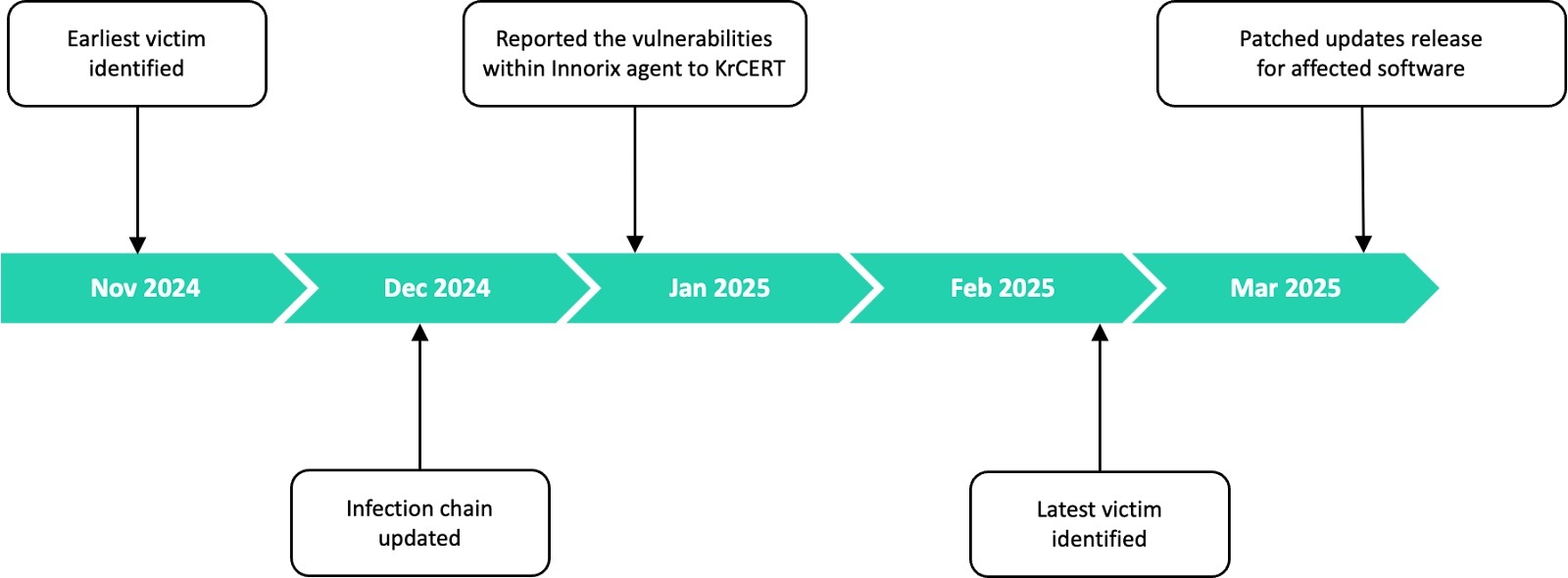
At least six organizations in South Korea have been targeted by the Lazarus Group as part of a campaign dubbed Operation SyncHole. This operation exploited vulnerabilities in key software, primarily focusing on the software, IT, financial, semiconductor manufacturing, and telecommunications sectors. The earliest signs of compromise were detected in November 2024.
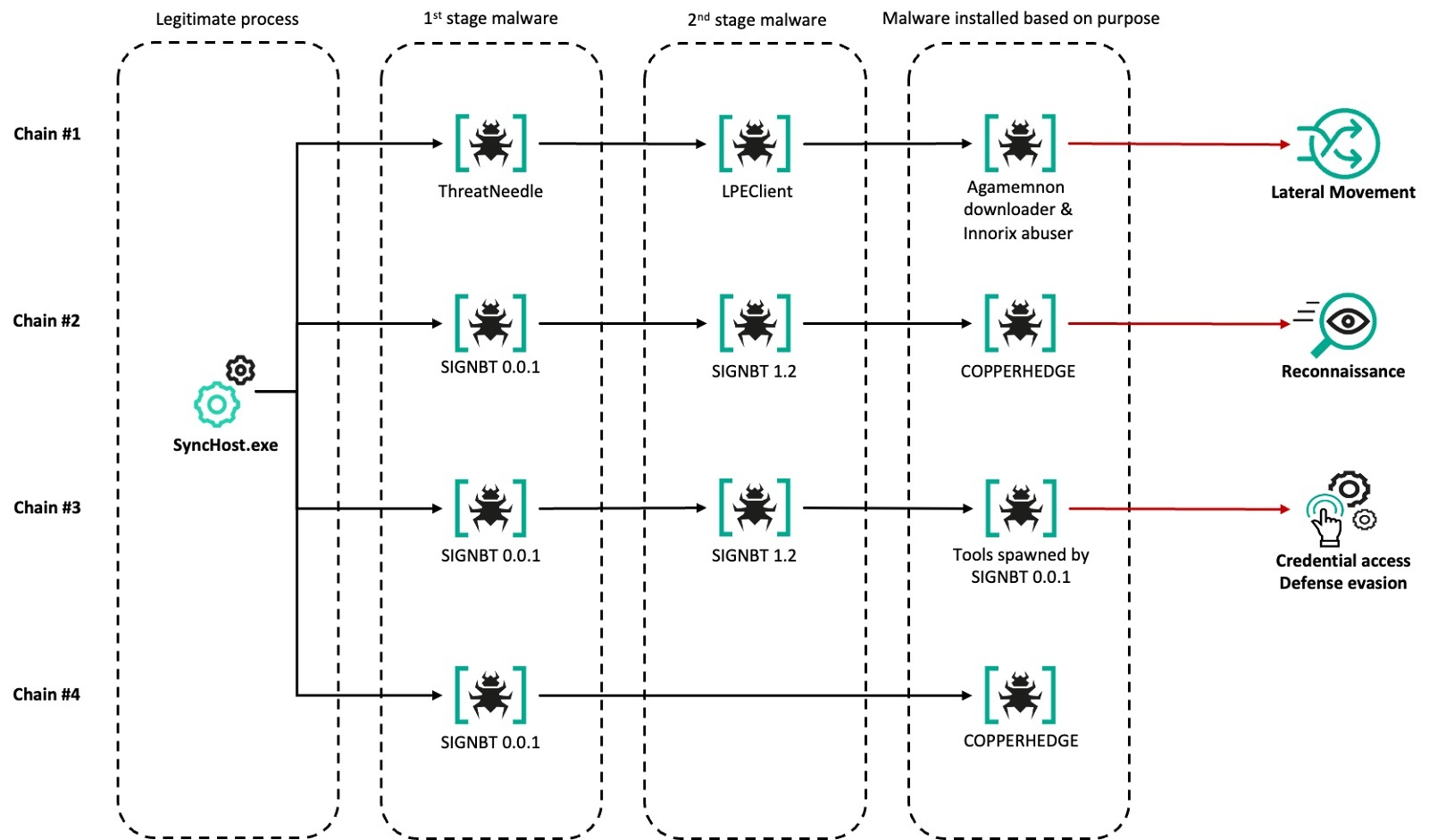
The attacks utilized a combination of a watering hole strategy and exploitation of vulnerabilities in South Korean software. According to researchers Sojun Ryu and Vasily Berdnikov, "A one-day vulnerability in Innorix Agent was also used for lateral movement." These techniques enabled the deployment of variants of known Lazarus malware such as ThreatNeedle, wAgent, and SIGNBT.
The exploitation of vulnerabilities in software, such as Cross EX, which is commonly used in South Korea for online banking and government applications, is a significant aspect of Lazarus's operational strategy. They have demonstrated a strong understanding of how to combine vulnerabilities with watering hole attacks, effectively targeting their victims.
Exploitation Techniques
The initial infection vector involved accessing several South Korean online media sites. When users visited these sites, they were redirected to malicious domains where malware was deployed. Researchers noted that "the script then ultimately executed the legitimate SyncHost.exe and injected a shellcode that loaded a variant of ThreatNeedle into that process."
The infection sequence was structured into two phases, with the first phase focusing on executing ThreatNeedle and wAgent, followed by the second phase using SIGNBT and COPPERHEDGE. These tools were employed for various tasks, including establishing persistence, conducting reconnaissance, and delivering credential dumping tools on compromised hosts.
Zero-Day Vulnerabilities
The Lazarus Group's campaign also highlighted significant zero-day vulnerabilities. For instance, a security flaw in the Innorix Agent was identified, which allowed it to facilitate lateral movement within networks. Kaspersky reported that they discovered an additional arbitrary file download zero-day vulnerability in Innorix Agent that has since been patched.
The ability to exploit vulnerabilities in software developed in South Korea is critical to the Lazarus Group's strategy. Researchers emphasized that the group is likely to continue targeting South Korean supply chains, indicating an ongoing risk for organizations in the region.
Social Engineering and Malware Integration
In addition to traditional malware attacks, the Lazarus Group has employed social engineering techniques to enhance their operations. A recent campaign involved the use of fake job offers through the “ClickFake Interview” technique to target cryptocurrency firms. This method allowed attackers to deploy a custom GolangGhost backdoor, showcasing their ability to blend espionage with financial theft.

A fake cryptogame website that exploited a zero-day vulnerability to install spyware
Kaspersky’s Global Research and Analysis Team (GReAT) noted, "While we’ve seen APT actors pursuing financial gain before, this campaign was unique." Their innovative approach, including the use of generative AI to create fake promotional content, demonstrates a significant evolution in their attack strategies.
Call to Action
Organizations must remain vigilant against the evolving tactics employed by the Lazarus Group and similar threat actors. Advanced threat detection and timely vulnerability patching are necessary to safeguard against these sophisticated attacks.
GrackerAI, an AI-powered cybersecurity marketing platform, can help your organization transform security news into strategic content opportunities. By automating insight generation from industry developments, GrackerAI enables marketing teams to identify emerging trends, monitor threats, and produce technically relevant content. Explore our services at GrackerAI or contact us to learn more about how we can assist your organization in navigating the cybersecurity landscape.




