LockBit Revelations Following Major Takedown

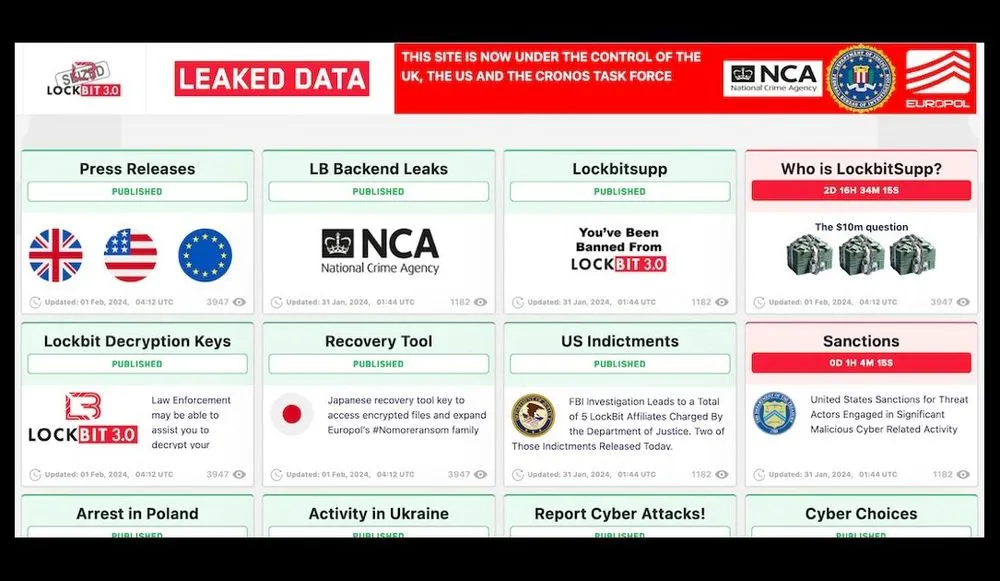
Image courtesy of The Record from Recorded Future News
An international coalition of law enforcement agencies, led by Britain’s National Crime Agency (NCA), announced unprecedented access to LockBit’s systems after dismantling the ransomware group. The operation disrupted their infrastructure and officials plan to release detailed insights throughout the week. The LockBit website has since been replaced with a splash page, indicating the severe impact of the operation on their operations.
During a press conference, NCA director Graeme Biggar confirmed the extensive intelligence collected, including decryption keys and information on the gang's users. Authorities have made arrests in Ukraine and Poland, with more anticipated as the investigation continues. The NCA, FBI, and Europol are collaborating to target remaining members of the gang.
Officials indicated that while some remnants of LockBit might still operate, the core service has been dismantled. This operation follows earlier law enforcement actions in the U.S., France, and the Netherlands.

Image courtesy of The Record from Recorded Future News
LockBit's Operations and Financial Impact
LockBit has been a significant player in the ransomware-as-a-service (RaaS) ecosystem, facilitating criminals in encrypting and extorting fees from victims. The group has been linked to over 2,000 victims, accounting for a substantial portion of ransomware attacks globally.
The gang's financial model includes a 20% take of the ransom paid by victims, with reported earnings exceeding $120 million over its operational period. Despite claiming to protect certain institutions from attacks, LockBit has been involved in incidents affecting hospitals, leading to critical operational disruptions.
Image courtesy of The Record from Recorded Future News
Emerging Challenges for LockBit
New insights reveal that LockBit may be experiencing severe operational difficulties, including backend issues preventing the publication of stolen data. Analysts report that the gang struggles with server storage, leading to empty threats against victims who refuse to pay ransoms. This indicates a potential decline in their extortion capability, as victims may no longer fear data leaks.
Jon DiMaggio from Analyst1 noted that the gang's inability to act on threats could deter future payments from victims. The prospect of shifting to alternative data-sharing methods, like torrents, poses a threat to LockBit's business model, which relies on maintaining control over victim data.
LockBit's Response to Law Enforcement Pressure
Following the takedown, LockBit's leader, known as "LockBitSupp," issued a statement indicating a shift in focus towards government targets. The gang claims to possess sensitive data, including court documents related to the election subversion case against former U.S. President Donald Trump.
LockBitSupp attributed recent vulnerabilities to personal negligence in maintaining their infrastructure, specifically a failure to update PHP, which allowed law enforcement access to their servers. This admission indicates significant internal issues within the gang, likely affecting their ability to operate efficiently.
GrackerAI's Role in Cybersecurity Marketing
In periods of heightened threat, organizations must stay informed and agile. GrackerAI offers an AI-powered cybersecurity marketing platform, enabling businesses to transform security news into strategic content opportunities. The tool supports marketing teams in identifying trends, monitoring threats, and creating relevant content that resonates with cybersecurity professionals.
By automating insight generation from critical industry developments, GrackerAI positions itself as an essential solution for creating timely and targeted marketing materials. Learn more about our services at GrackerAI or contact us to explore how we can support your cybersecurity marketing needs. Visit our website at https://gracker.ai.




