M&S Cyber Attack Overview


Image courtesy of Computer Weekly
Marks and Spencer (M&S) has been facing a significant cyber attack linked to the Scattered Spider hacking collective, which has disrupted its systems and caused serious operational issues. Reports suggest that Scattered Spider may have compromised M&S's systems back in February 2025, gaining access to sensitive files such as the NTDS.dit file, which contains critical information for Windows Active Directory operations. This breach has allowed the attackers to infiltrate M&S's Windows domain and deploy a ransomware called DragonForce, which has severely affected M&S's e-commerce capabilities and contactless payment systems.
According to Bleeping Computer, the initial disruption began on April 22, 2025, leaving customers unable to use click-and-collect services and forcing M&S to suspend online shopping. The attack has resulted in substantial financial losses, with reports indicating potential ransom demands around £10 million. M&S has sought assistance from cybersecurity firms including Microsoft and CrowdStrike to manage the incident.
Details of the Incident

Image courtesy of Retail Gazette
The cyber incident has been characterized as a ransomware attack, which involves hackers locking access to a company's data until a ransom is paid. M&S's Chief Executive, Stuart Machin, stated that the company is making necessary adjustments to its operations to manage the situation. External cybersecurity experts are involved in the investigation and recovery process, and M&S has reported the incident to the UK’s National Cyber Security Centre (NCSC). In-store services have also been impacted, with disruptions to contactless payments and gift card usage noted.
M&S has communicated that there is no immediate action required from customers, although they have been advised to remain vigilant regarding their personal information. Security experts have indicated that the ongoing nature of the incident suggests it is likely a sophisticated ransomware event. Professor Alan Woodward from Surrey University noted that recovering from such a complex attack takes significant time and expertise, especially given M&S's extensive operational systems.
Nature of Scattered Spider

Image courtesy of BBC News
Scattered Spider is noted for its unique structure, comprising mainly English-speaking members, and operates more like a loosely connected network than a traditional organized crime group. The collective has previously been involved in high-profile attacks and is known for its aggressive tactics. Trend Micro's Robert McArdle described their operational style, likening it to hacktivist groups such as Anonymous.
The growing threat from Anglophone cybercriminals like Scattered Spider poses significant challenges for organizations. Their attacks are often characterized by brazen methods, including threats to individuals associated with victims, as reported in various incidents.
M&S Response and Recovery Challenges
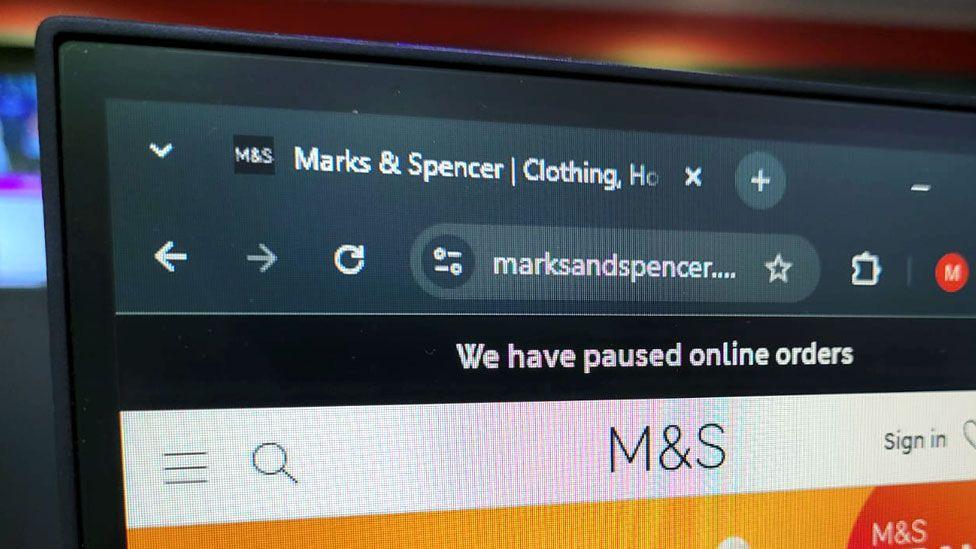
Image courtesy of BBC News
M&S's response to the attack has included pausing online orders and deliveries, leading to empty shelves in some stores. The retailer has not disclosed specific details about the attack's nature or the timeline for recovery, leading to speculation about the severity of the breach. Experts suggest that ransomware incidents like this can severely disrupt operations and require extensive effort and expertise to contain and resolve.
Cybersecurity professionals recommend against paying the ransom, as it does not guarantee data recovery and may encourage further attacks. It is essential for businesses to have robust cybersecurity measures in place, including real-time monitoring and threat detection, to minimize the risks associated with such breaches.
In the face of this challenge, companies like GrackerAI offer AI-powered cybersecurity marketing solutions that can help organizations transform security news into strategic content opportunities. By leveraging insights from incidents like the M&S cyber attack, GrackerAI enables marketing teams to stay ahead of emerging trends and craft targeted communications that resonate with cybersecurity professionals and decision-makers.
Explore GrackerAI's services to enhance your cybersecurity marketing strategy and stay informed about industry developments: GrackerAI.



