Data Breach of North Carolina Student Records
Incident Overview
PowerSchool, a data management contractor for North Carolina schools, faced a significant breach that exposed the records of millions of students and teachers worldwide. State education officials reported that public school employees received threatening messages from unknown individuals claiming to have access to the compromised data. Despite earlier assurances from PowerSchool that the situation was under control, the recent threats indicate that the data is now in the hands of malicious actors.

Image courtesy of Bladen Online
Breach Details
The breach was first disclosed in January 2025, revealing that the hacker had accessed sensitive records, including over 300,000 social security numbers. PowerSchool initially claimed that the situation was contained after paying a ransom to the hacker and watching a video of the data deletion. However, experts caution that there is no guarantee that the data was not copied before deletion.
PowerSchool has stated, “We do not believe this is a new incident, as samples of data match the data previously stolen in December.” The North Carolina Department of Public Instruction (DPI) has notified law enforcement and is currently investigating the incident.
For more details, visit:
Response and Implications
The DPI has advised school employees who received threatening emails to report them immediately. PowerSchool's data breach has raised significant concerns among parents regarding the security of their children’s information. Cybersecurity consultants have warned that children are particularly vulnerable to identity theft due to a lack of regular credit monitoring.
In response, PowerSchool is offering identity protection services, including credit monitoring for affected individuals. The company stated, “We sincerely regret these developments. It pains us that our customers are being threatened and re-victimized by bad actors.”
For more on identity protection, refer to:
Security Challenges in Education
The PowerSchool incident is part of a broader trend of increasing cyberattacks targeting K-12 institutions. Reports indicate that 80% of IT professionals in education experienced ransomware attacks in 2023. Cybersecurity experts emphasize that the lack of multifactor authentication and other security measures made it easier for hackers to access sensitive data.
Doug Levin, director of K12 Security Information Exchange, noted, “There’s no way to guarantee that the compromised data wasn’t downloaded and distributed to the wrong people.” The rise in identity theft among minors is a significant concern, as children typically do not monitor their credit.
For further insights, check:
Future Steps for North Carolina Schools
In light of the breach, North Carolina public schools will transition to using Infinite Campus for data management starting July 1. This decision reflects DPI's preference for a system with an improved security infrastructure. PowerSchool has contested this decision, appealing the decision while emphasizing its compliance with state laws regarding data protection.
As schools look to improve their cybersecurity measures, it’s crucial for organizations to consider robust solutions for monitoring and managing threats. GrackerAI offers a solution for cybersecurity marketing, designed to help organizations transform security news into strategic content opportunities.
For more information on how GrackerAI can assist in cybersecurity content creation and threat monitoring, visit GrackerAI.
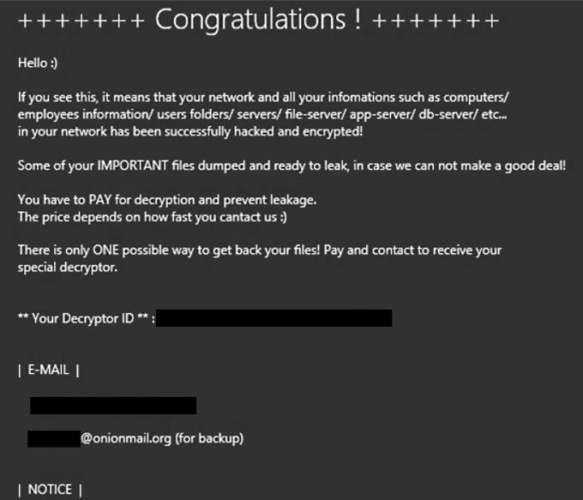
Image courtesy of The 74
Conclusion
The PowerSchool data breach highlights the critical need for enhanced cybersecurity measures in educational institutions. As the threat landscape continues to evolve, organizations must remain vigilant in their security practices and consider leveraging advanced tools to protect sensitive data. GrackerAI provides a comprehensive platform for cybersecurity marketing, helping organizations stay informed and proactive in addressing emerging threats. For more information, explore our services at GrackerAI.
Latest Cybersecurity Trends & Breaking News
Tricking AI into Creating Malware
Google TAG warns that Russian COLDRIVER APT is using a custom backdoor




