Cybersecurity Threats: Salt Typhoon and CL-STA-0048

Salt Typhoon Targeting Cisco Devices
China’s Salt Typhoon campaign has been actively breaching telecommunications companies, with researchers identifying attempts to compromise over 1,000 Cisco network devices globally. This includes targeting organizations in the U.S., South Africa, Italy, and Thailand. The group seems to have created a list of target devices based on their association with telecom networks. In December alone, the Insikt Group observed the hackers conducting reconnaissance on various IP addresses.

Image courtesy of The Record from Recorded Future News
More than half of the Cisco devices targeted by Salt Typhoon were located in the U.S., South America, and India. The group has also aimed at devices connected to universities across several countries, likely to access sensitive research in telecommunications and technology. U.S. officials have raised alarms about Salt Typhoon, noting breaches at nine major U.S. telecommunications companies, including Verizon and T-Mobile.
The hackers exploit unpatched vulnerabilities in Cisco devices, specifically targeting bugs such as CVE-2023-20198 and CVE-2023-20273. Insikt Group advised network administrators to monitor for potential exploitation, as the group has been seen scanning for vulnerable devices multiple times in December and January.
Vulnerabilities Exploited by Salt Typhoon
Salt Typhoon employs sophisticated tactics to exploit known vulnerabilities, which are crucial for gaining initial access to victim networks. The group has targeted the telecommunications sector extensively. The known CVEs exploited include CVE-2021-26855 (Microsoft Exchange) and CVE-2022-3236 (Sophos Firewall).
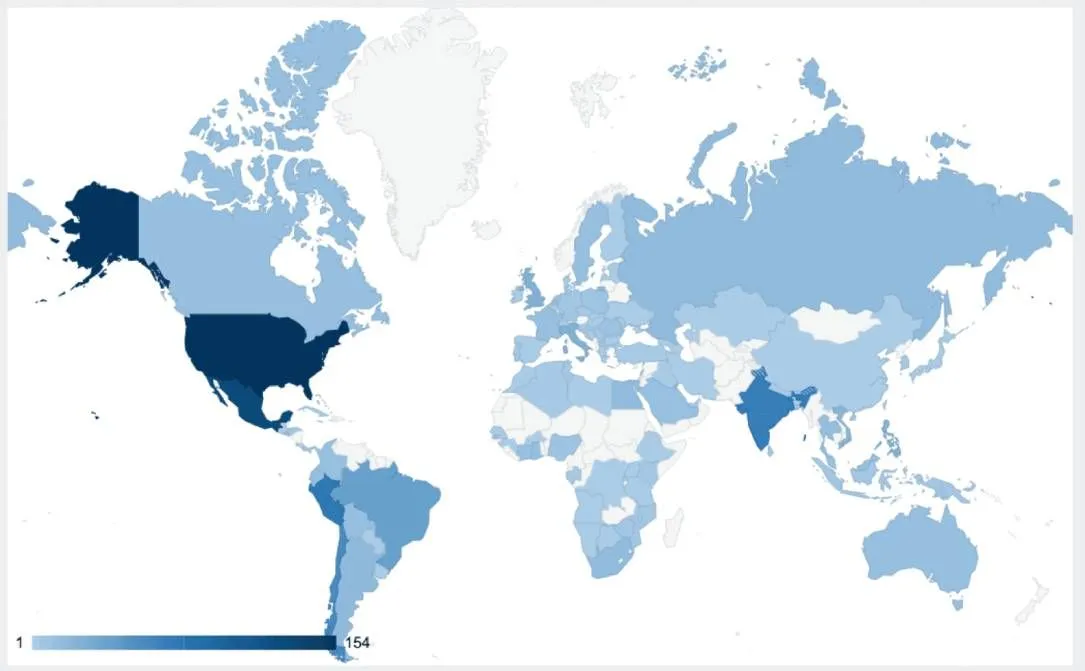
Image courtesy of Recorded Future
Despite patches being available, many organizations remain vulnerable. For instance, a staggering 91% of devices impacted by ProxyLogon remain unpatched. The focus on securing Cisco devices is critical, as CISA has urged organizations to disable Cisco’s Smart Install service, which is commonly abused by attackers.
CL-STA-0048: Espionage in South Asia
The CL-STA-0048 espionage campaign has been identified as targeting high-value entities in South Asia, using advanced techniques like DNS exfiltration. This operation aimed to steal personal information from government employees and sensitive data from telecommunications organizations.
The threat actors exploited vulnerabilities across various services, including IIS, Apache Tomcat, and MSSQL. They demonstrated a methodical approach by targeting public-facing servers and using rare tools for data exfiltration. Such activities underscore the necessity for organizations to prioritize patching and adhere to best practices in IT hygiene.
Techniques and Tools Used by CL-STA-0048
The campaign utilized the PlugX backdoor, a well-known remote access tool, to maintain persistent access. The attackers employed a method known as Hex Staging to deliver payloads in chunks, resulting in a complex infiltration process.
The usage of tools like PowerShell for reconnaissance and the SQLcmd utility for data theft exemplifies the sophistication of the group. Their activities highlight the urgent need for robust cybersecurity measures to defend against such advanced persistent threats.
Enhancing Cybersecurity with GrackerAI
Organizations must remain vigilant against sophisticated threats like Salt Typhoon and CL-STA-0048. GrackerAI, an AI-powered cybersecurity marketing platform, helps organizations transform security news into strategic content opportunities. By leveraging GrackerAI, marketing teams can identify emerging trends, monitor threats, and produce content that resonates with cybersecurity professionals.
For organizations looking to enhance their cybersecurity posture and marketing strategies, exploring the services offered by GrackerAI is essential. Visit GrackerAI to learn more or contact us for tailored solutions.



